Secure and Protect Microsoft 365/Azure
Learn how to protect your business and customer information from attacks
No one wants to be hacked, and No single security solution will solve your problems
It is a delicate balance between the security controls we need that enable productivity but do not compromise the organization. At Covenant, we see this problem every day. Fundamentally, we recommend you simplify your approach to complex security challenges by using native security capabilities that are built into your platform, devices, and productivity tools rather than products from different manufacturers that do not integrate.
Microsoft 365 Security Assessment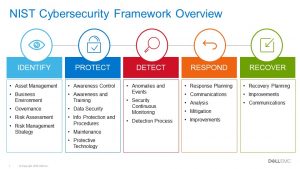
It is essential for every business to understand what technologies they do and do not have to protect their customers, employees, and reputation. The best way to understand all these moving parts is with a technology assessment.
One of Covenant’s senior architects will perform a thorough inspection of your Microsoft 365 environment We look at licensing, product configuration, security settings, and licensed products. The assessment can also be extended to your technology infrastructure to obtain a more holistic picture of your entire environment.
In the final report (sample provided), we provide a list of recommended changes and give a technical walkthrough to one or two of your technical staff, so they understand the findings in the report and where changes could/should be implemented. In the end, you receive real and actionable information that will better secure your employees, devices, and data.
A full Assessment typically takes 1-3 weeks to complete
Fortify
Based on the Assessment, your 365 licensing, and business requirements, Covenant starts the multi-phased Fortify processes by ensuring core 365/Azure security settings are in place. We then shift focus to better secure the identities, devices, and data you are responsible for.
Phase 1 – Non-user impacting changes. The primary focus is on Defender or email and endpoints.
Phase 2 – Implementing security changes that users will more readily see and interact with. Examples are self-service password reset, MFA, conditional access, and email forwarding policies
Phase 3 – Data protection, such as AIP, Sensitivity Labels, and Data Loss Prevention. These areas of security require business use case analysis and time with key business leaders.
The Fortify service can be provided without or integrated with an Assessment. It normally takes 3-8 weeks to fully implement all three phases.
Manage
Cloud services change fast which can be challenging for your internal IT staff keep up with. Covenant helps you take the complexity out of cloud so you can deliver well architected systems and a great user experience.
Covenant’s Cloud Architects and management team work to understand your business and help you architect, deploy, migrate and manage Microsoft 365, Azure, and AWS services.
Comply
As regulations to protect individual privacy and financial information grow, most businesses are required by law to comply with some form of information protection regulation.
Covenant works with your business leaders, technology team, and auditors to ensure your business has the appropriate documentation, training programs, technology protections, and auditing required to meet the regulatory requirements identified for your business. Covenant provides the Comply service in both on-demand and as an ongoing service.
